Welcome to the second of a three-part series designed to help organizations orient and rapidly protect against the latest cloud cyberattacks when leveraging Microsoft 365 services.
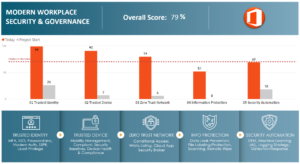
I’m dedicating this post to all the cyberdefenders who find themselves underrepresented, underbudgeted, understaffed and facing a growing threat landscape within their corporate firewalls. This is the exact situation at one of my clients when the sole security admin invited me to perform our proprietary assessments across both Azure and M365 services. As mentioned in the previous post, the result was staggering in that after years of being a successful online store business they had only achieved what’s depicted in the grey bars below for security posture:
The local cyberdefender knew many things were wrong,
“but did not have a way to visualize or measure the situation.”
Within days of our initial engagement, the organization experienced an intense and costly ransomware attack that deleted backups, locked resources and severely impacted revenue. Horizons went to work immediately assessing, prioritizing tasks into roadmaps and executing collaboratively, despite the ongoing disruptions from the persistent threat. The organization proved very motivated and green-lit all of our recommendations which are based on cloud security best practices and notes-from-the-field. The result was a rapid record-breaking deployment of the Microsoft 365 E5 stack represented by the orange bars above.
Getting to that “Minimum Standard” is difficult, espeically for mid-to-large size organizations with legacy technical debt or critical infrastructure. There’s no silver bullet in cybersecurity. The objective is
“to make it too expensive to target your environment.”
You do this through layering security controls which prevent or at least slow attacks from occuring. Malicious attackers have a billable rate. They need an return-on-investment for their efforts. Although it is becoming cheaper to find attackers for hire or tools for sale as illustrated below.
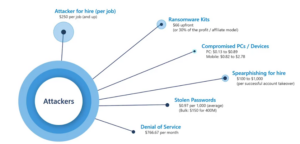
(Pic from Top 10 Best Practices for Azure Security)
If you suspect a persistent threat or are just looking to get started, it may be beneficial to just focus on the first three layers of cloud security defense illustrated below.

Trusted Identity is at the top and represents the highest priority as well as best defense against cybersecurity threats. With identities publicly accessible, they are the number one attack surface for credential compromise. Eliminating legacy auth, enforcing Modern Auth, Azure AD federation, MFA and Self-Service Password Reset some of the baseline tasks every organization should have in-place today.
Trusted Devices is the second layer. Remember that there is no silver bullet technology with cybersecurity. Rather the goal is to layer defenses in so that malicious actors find it too expensive or cumbersome to stay for long. If they persist, layered defenses can slow and alert to their activity. Trusted Devices first involves Azure AD establishing what is a “Corporate” device versus a “Personal.” Admins then lockdown access based on “Corporate” device states indicated by things like Hybrid Domain Join, Azure AD Join, Intune MDM enrollment and compliance, etc. Windows devices also have hundreds of security controls disabled (although Windows 11 is changing that story). Cloud Security Baselines should be implemented to eliminate legacy backdoors and ensure the best security features are enabled and fully functioning.
Zero Trust Network is the third layer and largely is made possible by the work accomplished in the first two. Here Azure AD conditional access is implemented to ensure all identities and devices are challenged and verified in multiple ways before access is granted. A good Cloud App Security Broker works at this layer as well, providing advanced access and sharing features. Gone are the days of trusting everyone behind an IP, firewall or corporate network.
At least this story had a happy ending. The client took matters seriously and rapidly deployed security workloads in Microsoft 365, desktops, servers and Azure. Some of our clients take years to achieve what is depicted by the orange bars above. It was an amazing cultural shift that continues to thrive today.
Horizons does cloud security and automation baselines for our clients as standard. We’re fast, efficient and can be leveraged for establishing a 6 month to multi-year roadmaps prioritized to the needs of the organization. Contact us today for an environment refresh following the latest standards or a quick assessment to feed future roadmaps tailored to your organization’s needs.



