As mid-sized businesses increasingly transition to the cloud, the critical role of a strong cloud security solution cannot be overstated. This move, while offering numerous benefits, also introduces significant concerns such as data breaches, misconfigurations, and insider threats. Fortunately, solutions like those offered by Microsoft Cloud Security are specifically tailored for small and medium-sized businesses (SMBs), providing a robust framework to address these challenges.
Understanding cloud security begins with recognizing the shared responsibility model. This model clearly defines what the cloud provider handles versus what the business must manage itself. Beyond internal management, mid-sized businesses also face significant regulatory pressure and compliance requirements from standards such as ISO 27017, HIPAA, and GDPR. Effective cloud security is not just about protection; it’s about meeting these crucial obligations.
Implementing a comprehensive cloud security strategy involves several core best practices:
It is essential to use reputable cloud providers such as Microsoft 365 and Azure. These platforms are widely recognized for being certified and compliant, offering a strong foundation for your cloud security posture.
As mentioned, a key aspect is to clarify the distinction between infrastructure and data control within the shared responsibility model. While the cloud provider secures the underlying infrastructure, your business remains responsible for securing your data and access to it.
Implementing Multi-Factor Authentication (MFA) is paramount, as it can lead to a 99.2% reduction in account compromise. Furthermore, adopting Zero Trust principles means that every access request is verified, regardless of whether it originates from inside or outside your network. This approach trusts no one by default and continuously verifies. Microsoft Entra ID helps in safeguarding against password loss or theft with advanced multifactor authentication.
Leveraging Microsoft Entra ID (formerly Azure Active Directory) is crucial for unified identity management. It allows you to enforce least-privilege access, conditional access policies, and centralized identity controls, ensuring that users only have the necessary permissions to perform their tasks. Microsoft Entra ID helps employees securely access business apps wherever they work.
Encrypting data both in transit and at rest is a fundamental security measure. You should encrypt sensitive information using strong cryptographic methods like AES-256 and TLS, and you can rely on Microsoft’s default encryption capabilities. Microsoft 365 Business Premium also includes the ability to encrypt emails and apply sensitivity labeling for files to prevent data loss.
Proactive threat detection is vital. Utilizing tools like Microsoft Sentinel or Microsoft Defender enables continuous monitoring and Security Information and Event Management (SIEM) capabilities. These solutions help in detecting and responding to sophisticated attacks by aggregating and analyzing security data from various cloud services.
Managing devices and enforcing security policies across all your endpoints is critical. Microsoft Intune helps manage devices across Windows, macOS, Linux, iOS, and Android platforms, while Microsoft Defender provides comprehensive endpoint protection. This combination helps safeguard against ransomware and other cyberthreats.
It is essential to periodically scan, test, and patch all your assets. This includes regularly updating cloud platforms and applications to protect against known vulnerabilities. Additionally, authorizing cloud penetration testing can help identify and remediate potential security gaps.
Effective data governance involves classifying sensitive data, applying policies like Microsoft Purview and Data Loss Prevention (DLP), and maintaining detailed audit trails. These measures help prevent unauthorized access, sharing, or loss of sensitive information and ensure compliance with regulatory requirements.
Your employees are often the first line of defense. It’s crucial to train staff in security hygiene and how to spot phishing attempts. Regular training and awareness programs can significantly reduce the risk of human error leading to security incidents.
Microsoft offers a suite of integrated tools designed specifically for SMBs:
This comprehensive bundle includes essential security features like MFA, Microsoft Defender, Microsoft Intune, and Microsoft Purview, alongside productivity apps. It protects against phishing and ransomware across email, collaboration apps, and endpoints.
These provide powerful SIEM capabilities for real-time threat detection and incident response across your cloud environment.
Offers unified identity management and is fundamental to implementing Zero Trust principles.
Safeguards devices against cyberthreats with AI-powered protection, including next-generation antivirus and endpoint detection and response (EDR). It supports up to 300 users and devices across Windows, MacOS, iOS, and Android.
Provides AI-powered protection against phishing attempts and malware for email and collaboration tools like Microsoft Teams, SharePoint, and OneDrive, featuring Safe Links and Safe Attachments.
Allows for unified management and protection of work devices across multiple platforms, helping to enforce security policies and remotely wipe data from lost or stolen devices.
Offers solutions for information protection, insider risk management, data loss prevention, and data governance.
These strategies integrate various security capabilities across cloud-native applications.

A structured approach ensures effective security deployment:
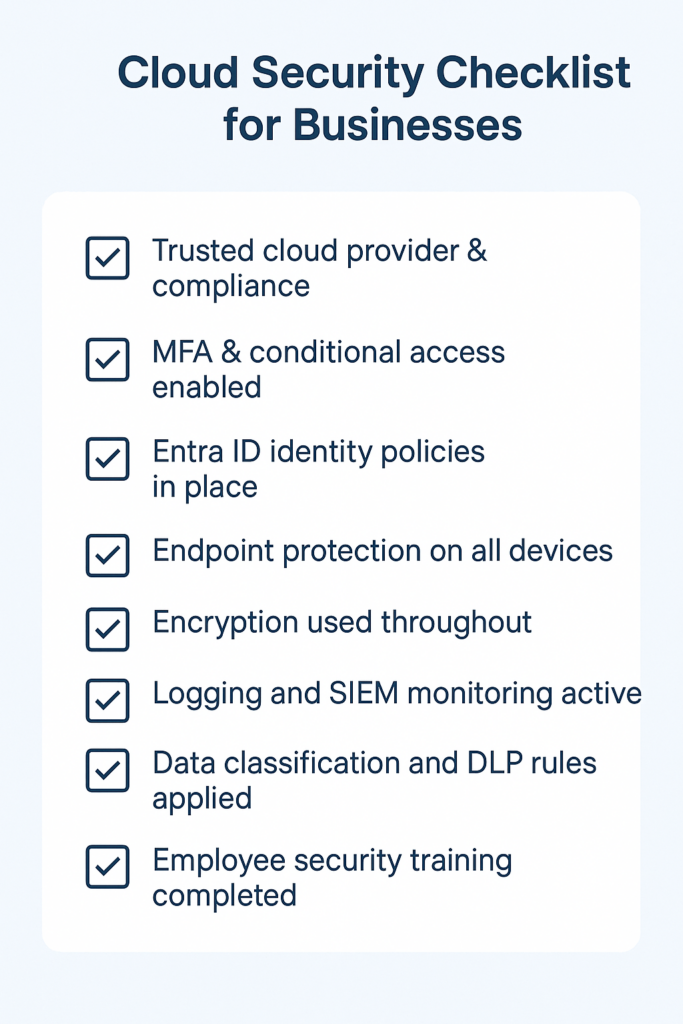
Here’s a quick checklist to help you scan your cloud security posture:
For mid-sized companies aiming to grow confidently, a robust cloud security solution is not just an option, but an essential requirement. Microsoft’s integrated approach emphasizes security built in, not merely bolted on, providing a cohesive and comprehensive defense strategy. We strongly encourage businesses to evaluate their current cloud posture, select the right tools for their specific needs, and consistently train their teams to foster a strong security-aware culture. By diligently implementing these best practices, your organization can navigate the complexities of cloud security and confidently embrace the cloud’s vast opportunities.